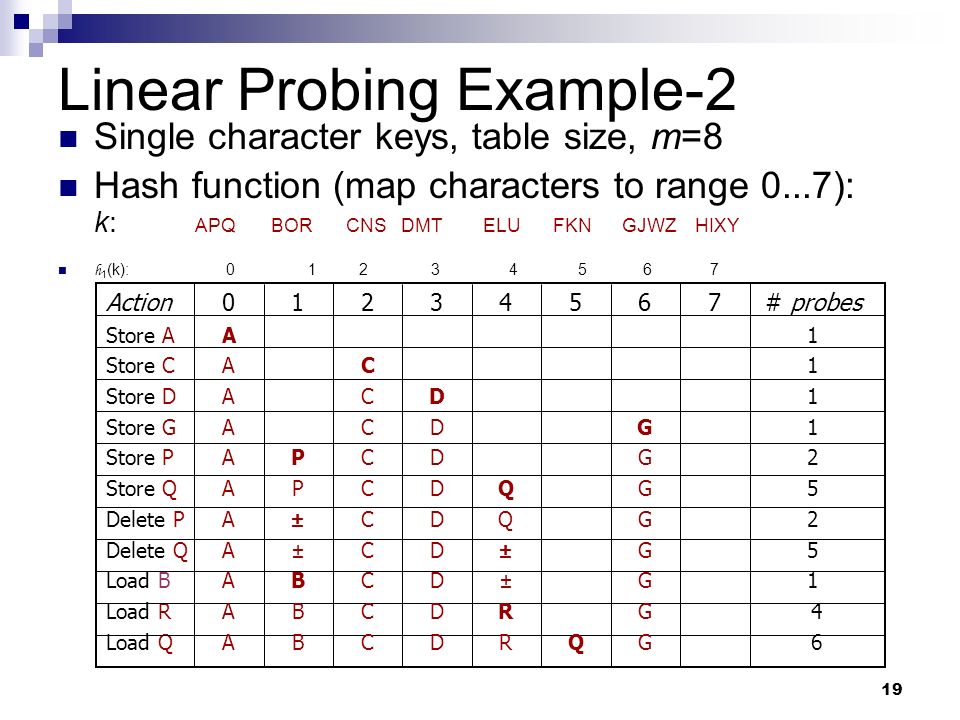
algorithm - Is searching a hashtable for a value that isn't there O(n)? (linear probing) - Stack Overflow

Hash tables with different form of collision resolution. Hash function... | Download Scientific Diagram

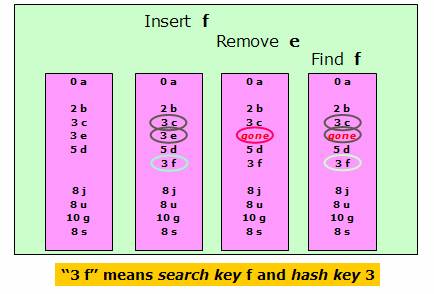
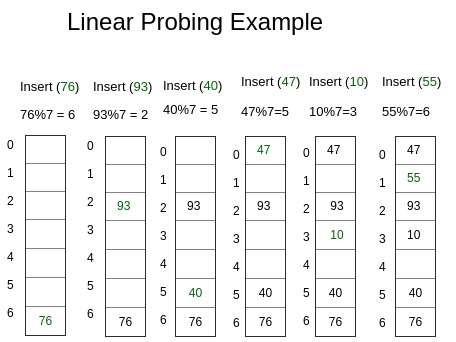
What needs to be done after deleting an item in a hash table built under opening addressing with linear probing - Computer Science Stack Exchange

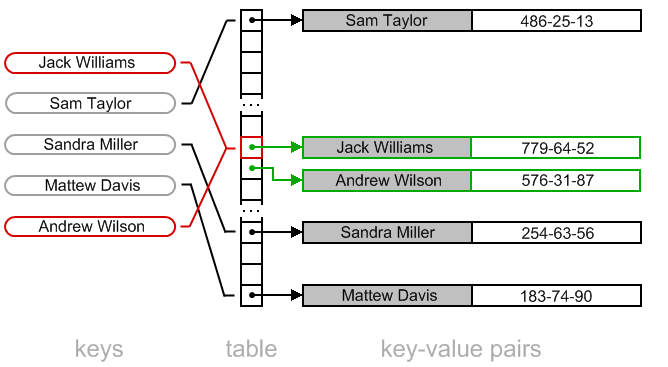
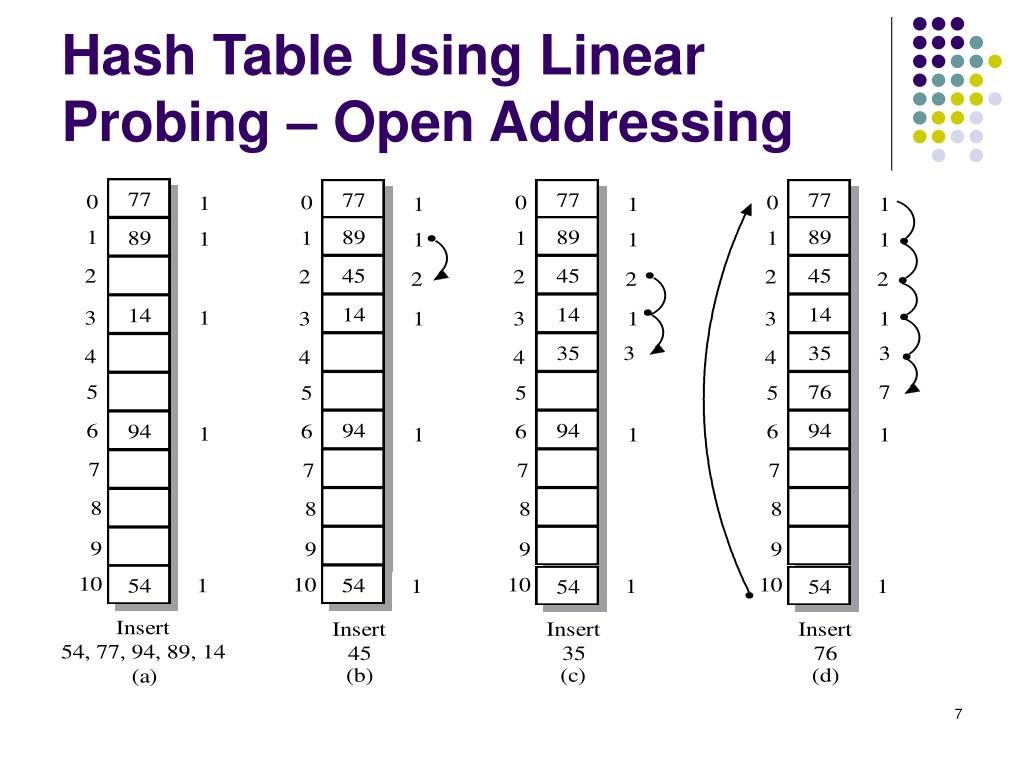
algorithms - Need help with adding elements to hashtable with linear probing - Computer Science Stack Exchange
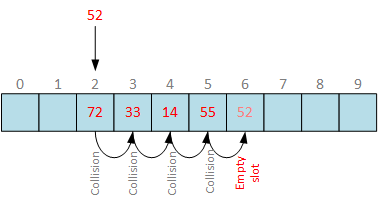
Solved] 7. (5 marks] Consider a hash table with 10 slots implemented using open addressing with linear probing; the auxiliary hash function is h'(k)... | Course Hero
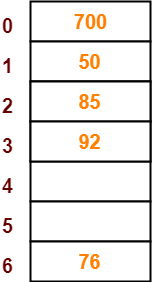
Solved] 2. Suppose you have the following hash table, implemented using linear probing. The hash function we are using is the identity function, Mac... | Course Hero