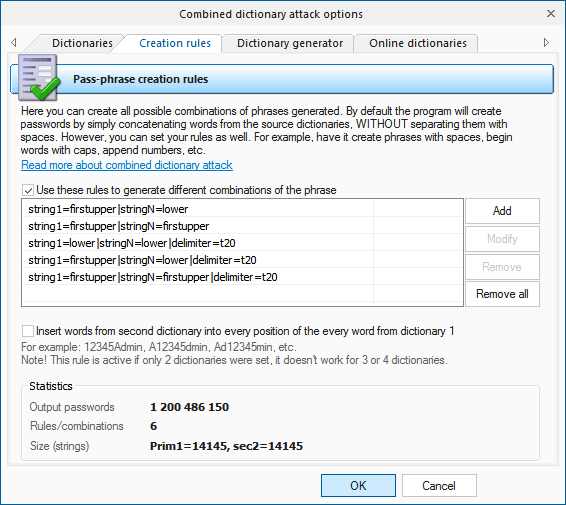
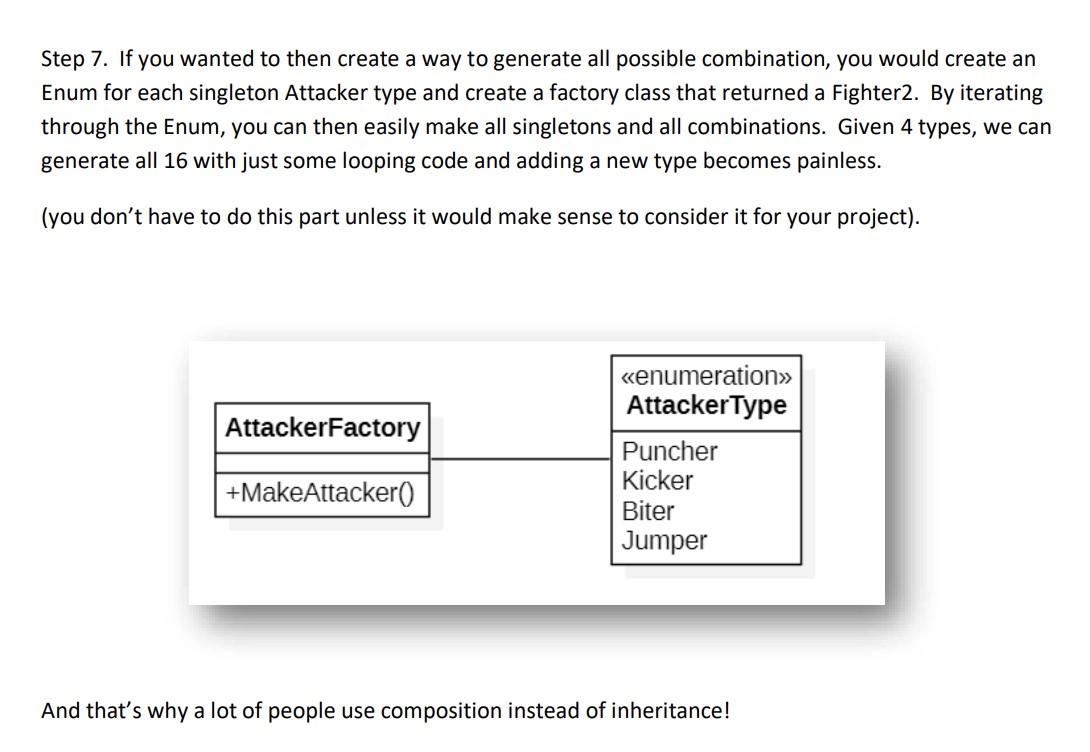
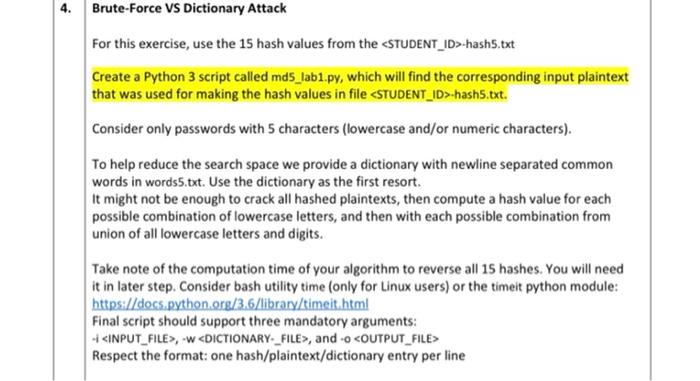
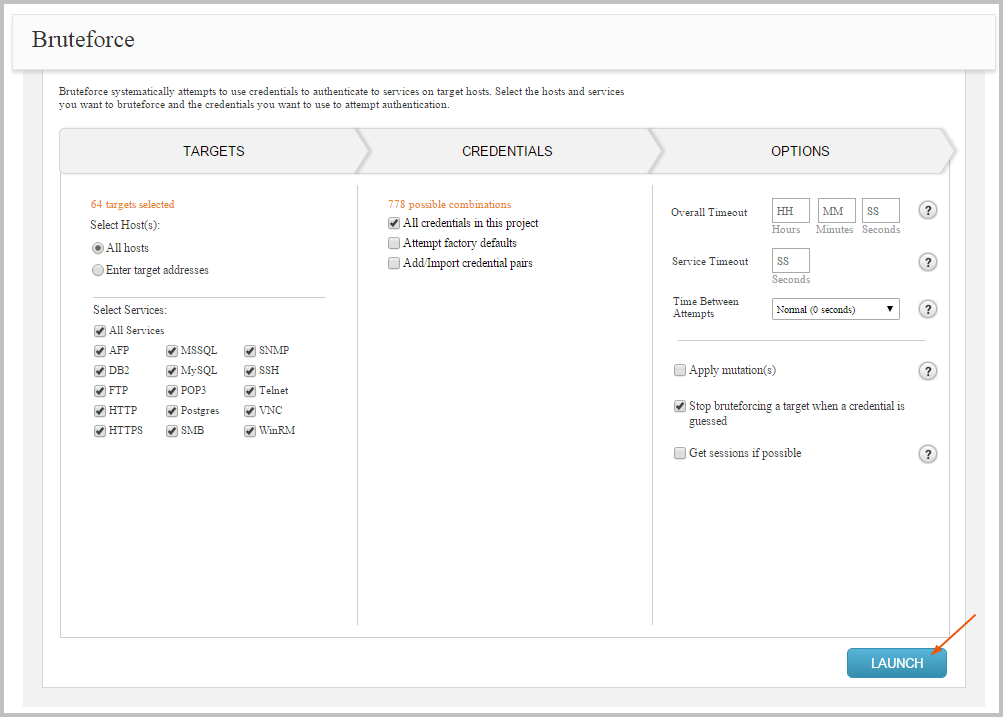
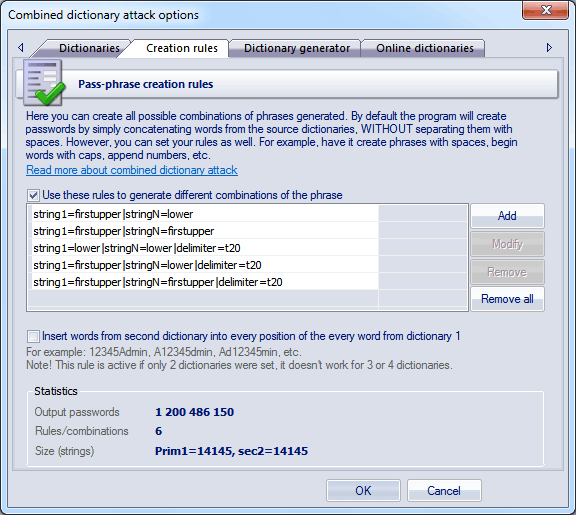
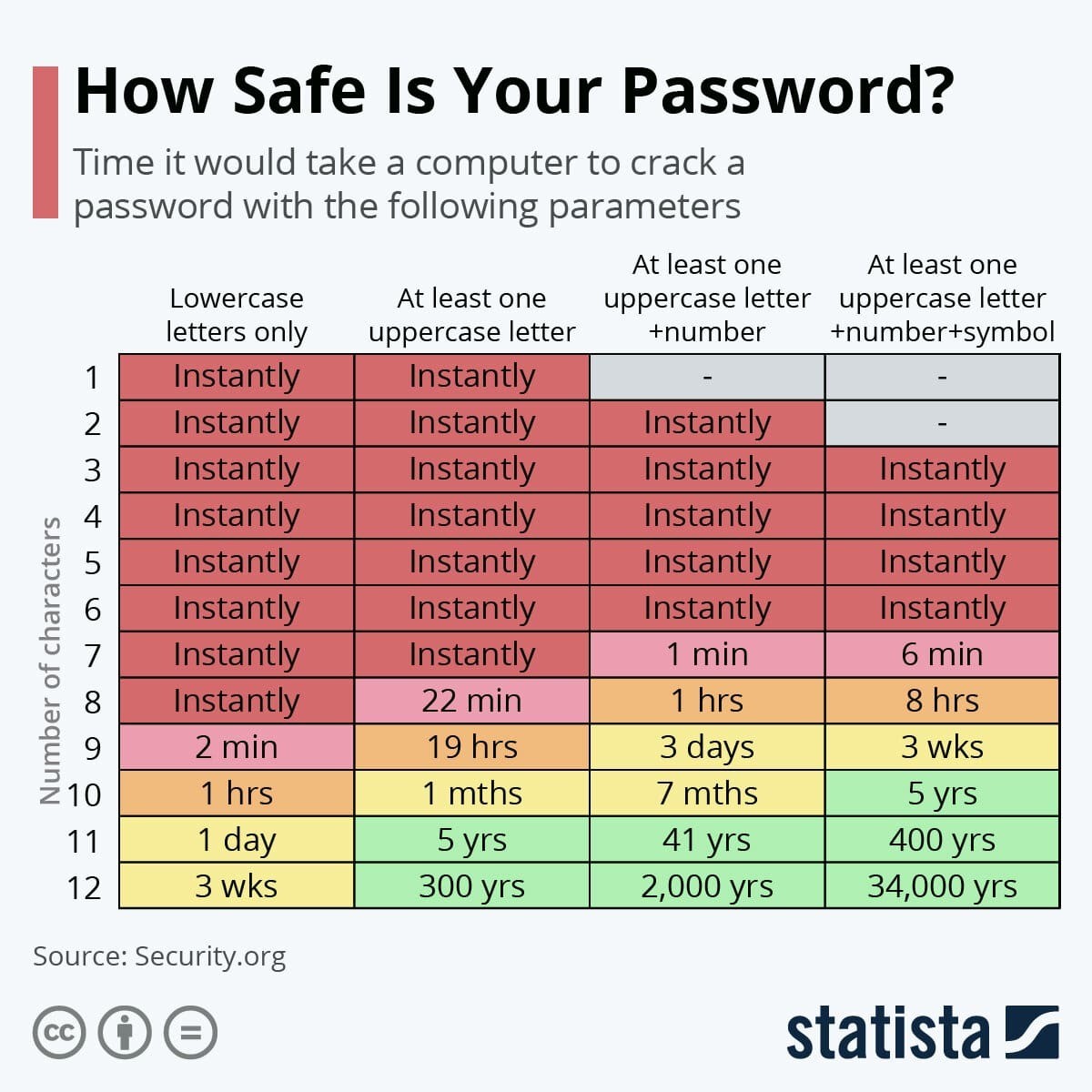
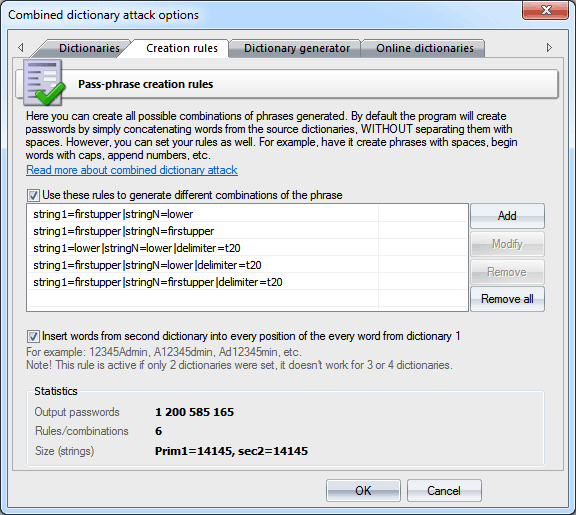
Class/attack accuracy breakdown for the 3 attack/generator setting.... | Download Scientific Diagram

MD5 & Hash Encryption By Alex Buzak. Overview Purpose of MD5 and Hash Encryptions Examples MD5 Algorithm Explanation of Possible Security Risks Practical. - ppt download
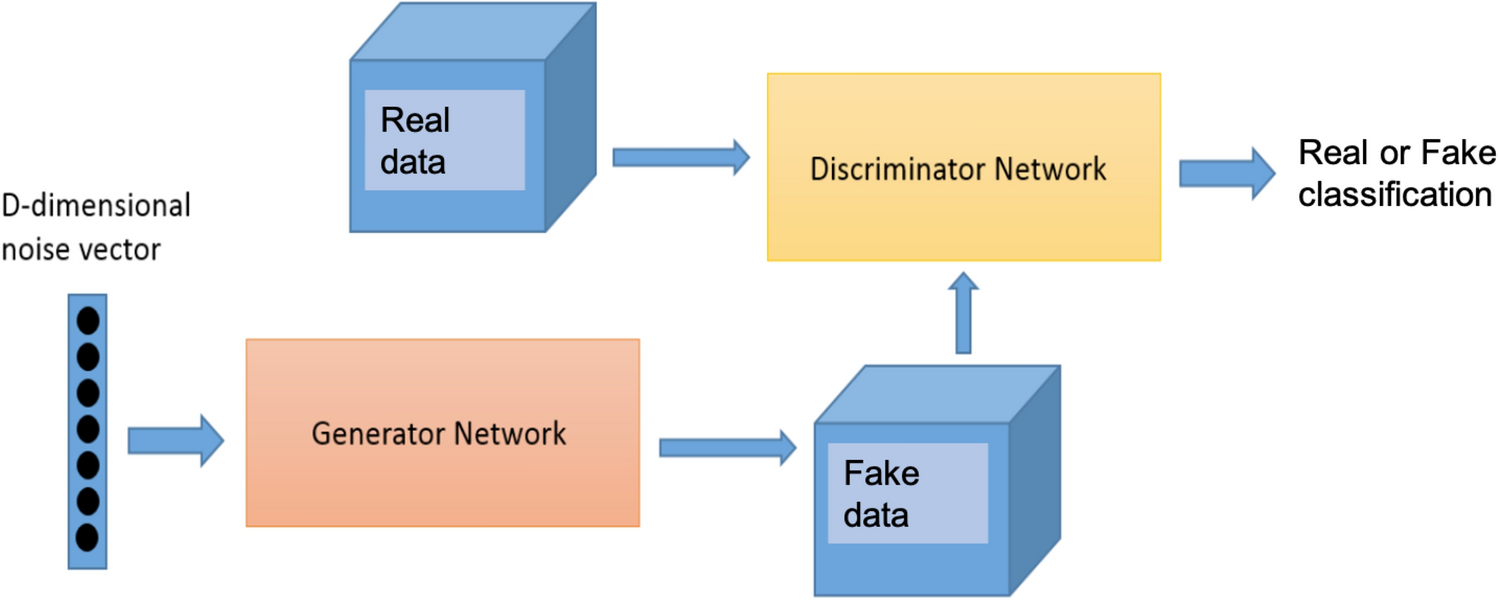
![PDF] Attacking the combination generator | Semantic Scholar PDF] Attacking the combination generator | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ea266e2624fbae8e1935028c3cad10b62b917815/8-Table1-1.png)