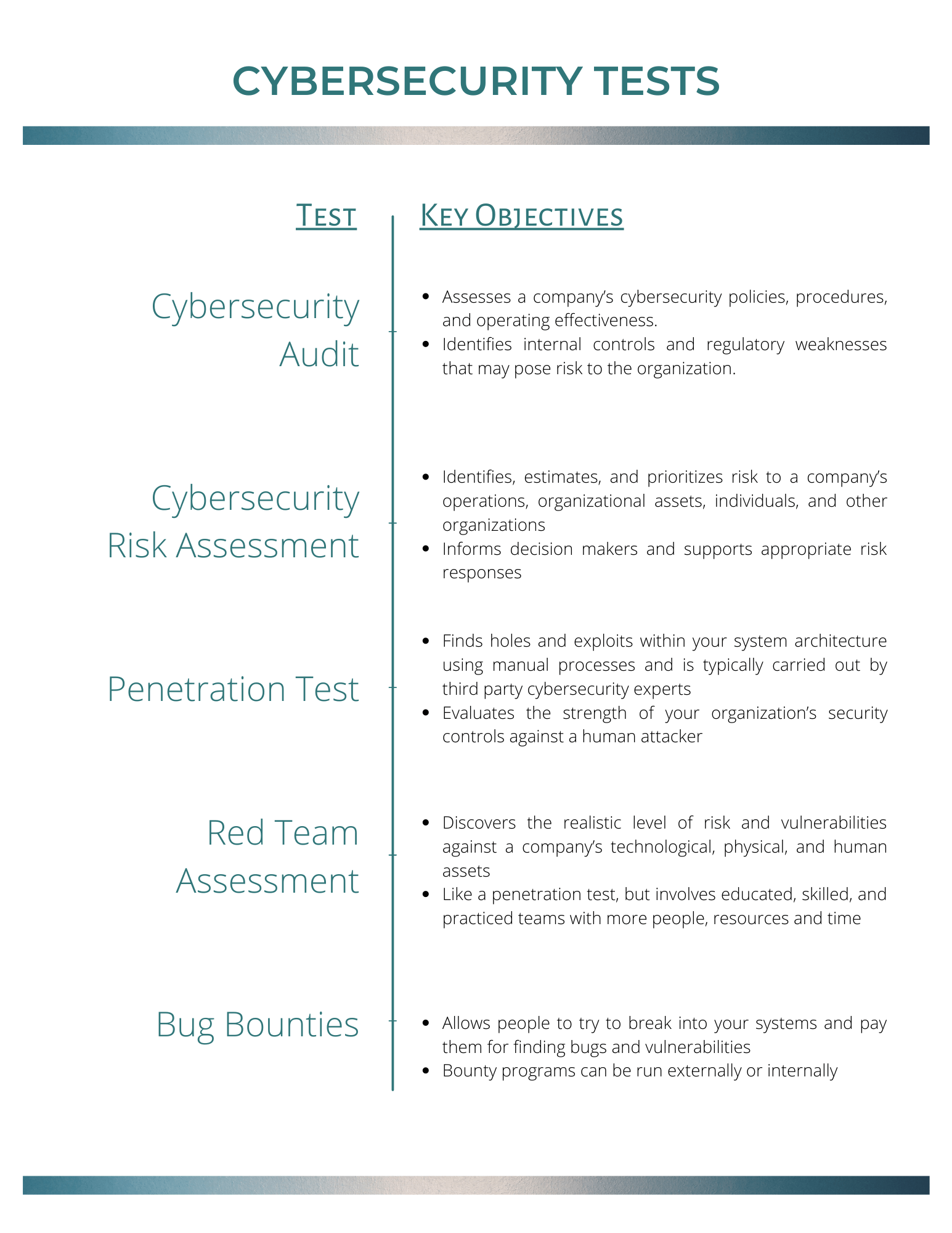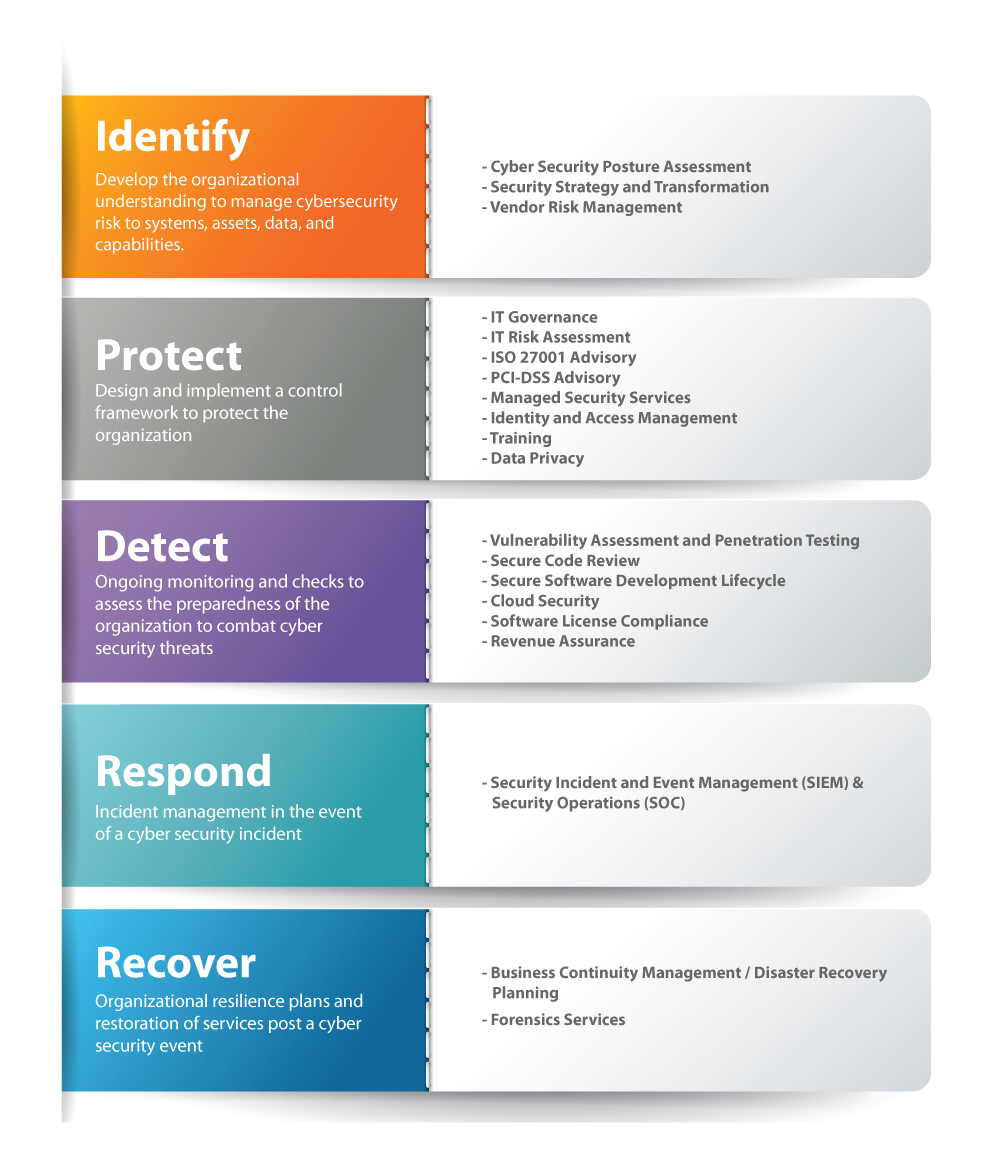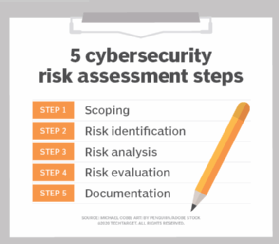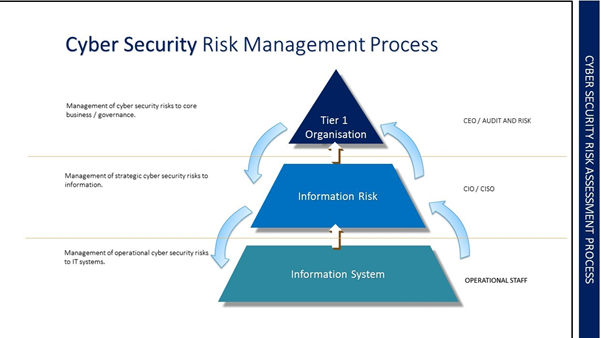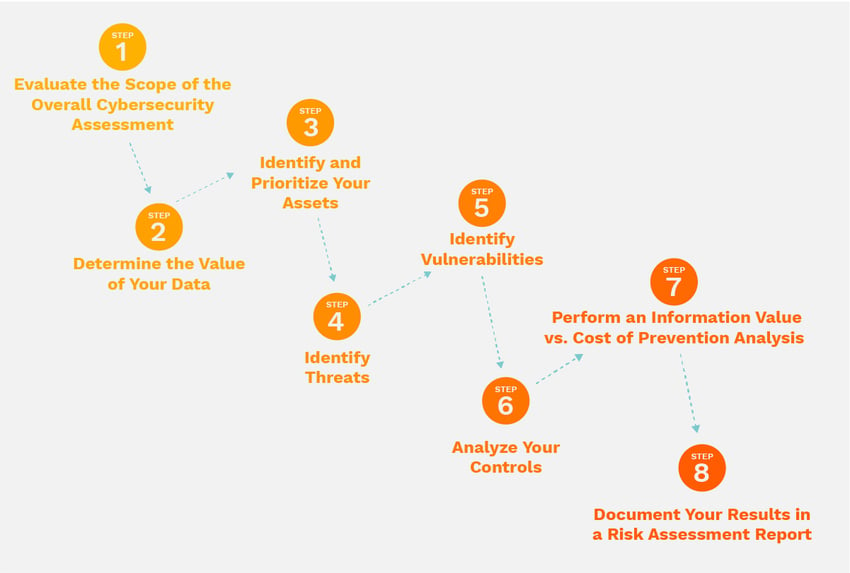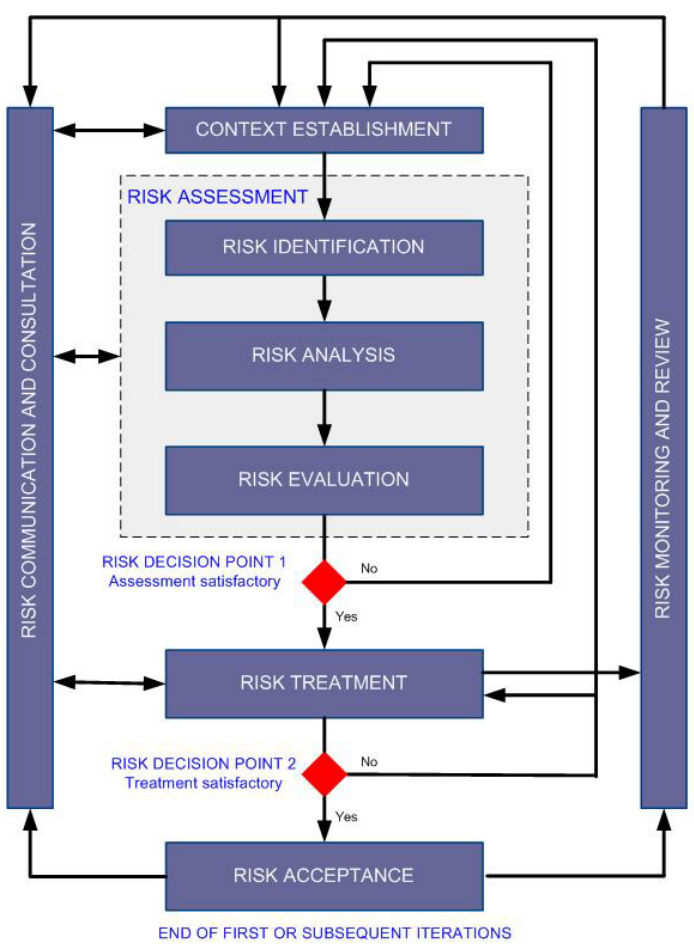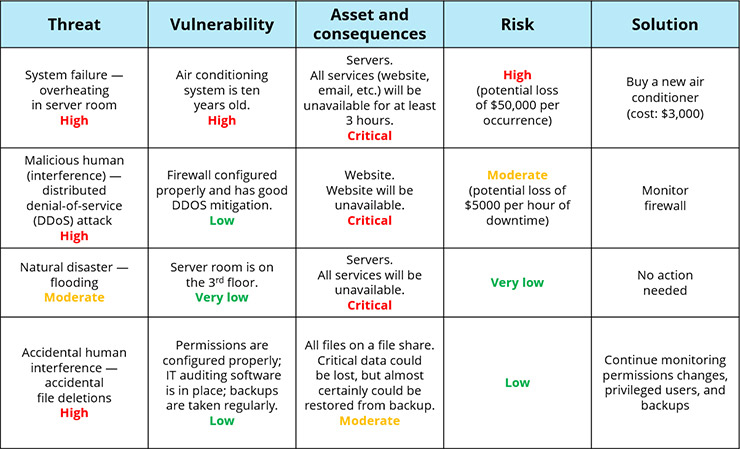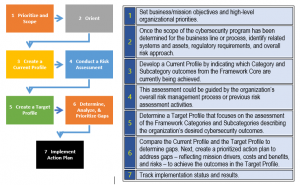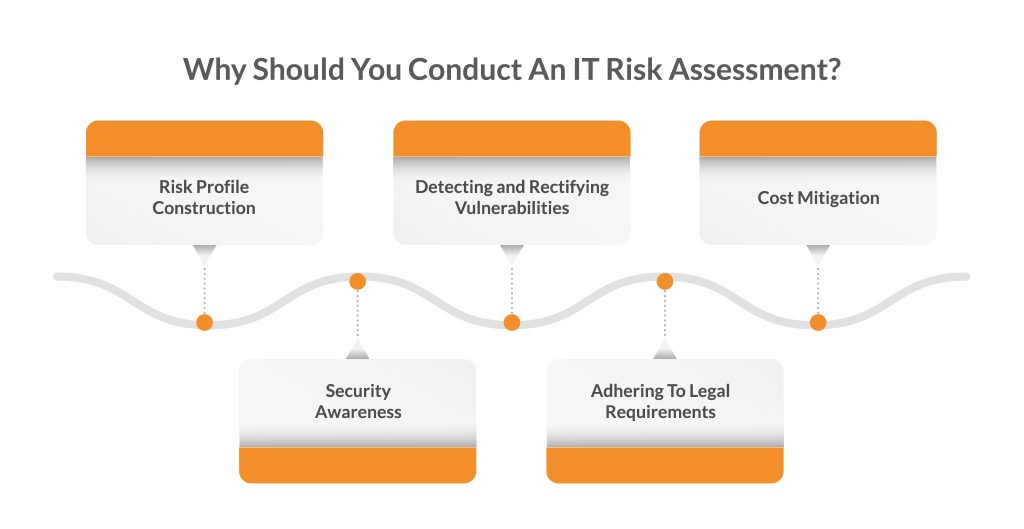
Risk Assessment: The Crucial Element Of A Successful Security Implementation Program - Security Boulevard
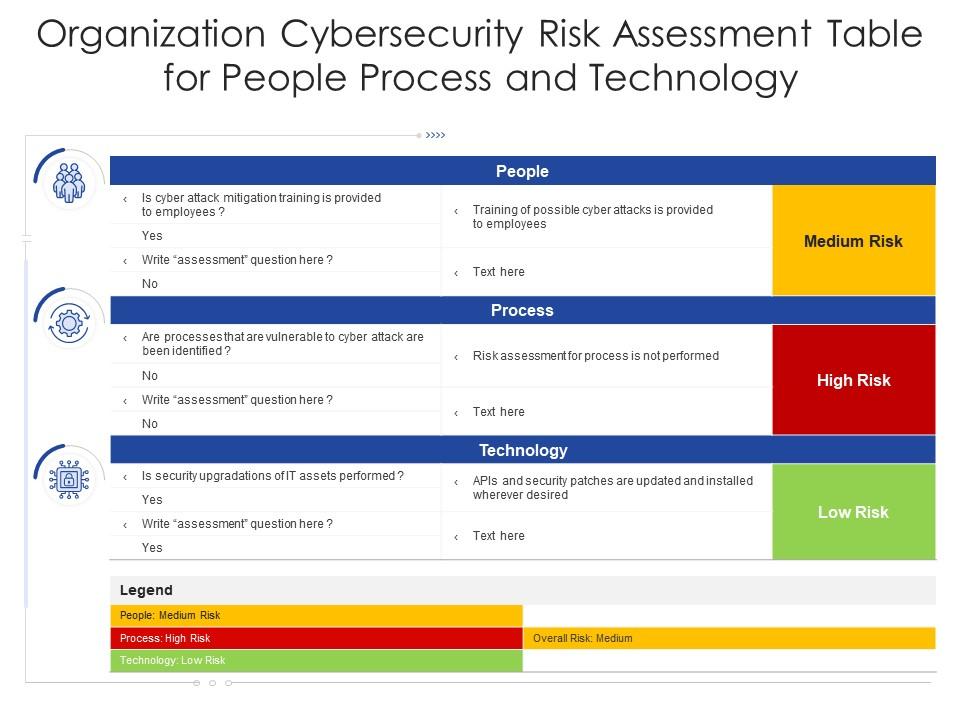
Organization Cybersecurity Risk Assessment Table For People Process And Technology | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Criteria for Selecting a Risk Assessment Methodology | by Eric Vanderburg | Security Thinking Cap | Medium